The concept of the Value Chain was first popularized by Michael Porter of Harvard Business School fame, in his groundbreaking book, Competitive Advantage: Creating and Sustaining Superior Performance back in 1985.
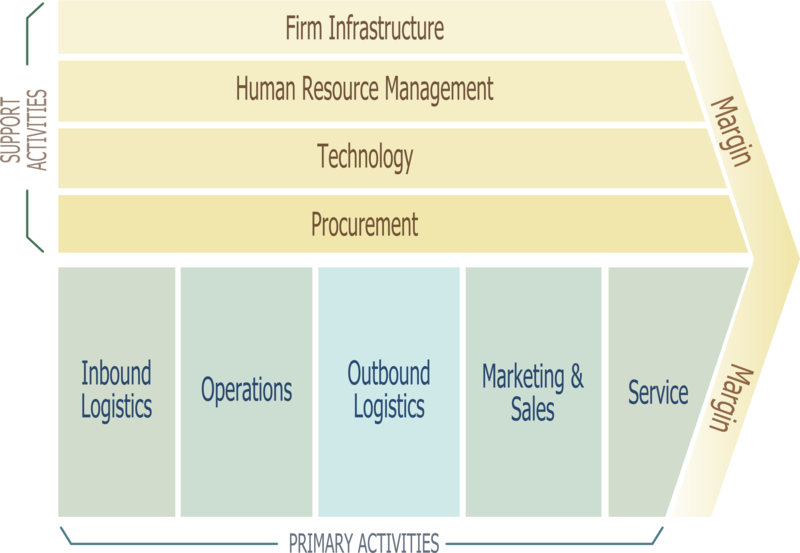
Source: http://en.wikipedia.org/wiki/File:Porter_Value_Chain.png
Those items across the top, labeled Support Activities, are those items that we usually just lump under the catch-all term of “overhead.” For our purposes in the Business Model of Security, we look at the Primary Activities and map these operations into our security program.
What is really interesting to uncover is where one Value Chain can feed another. For example, a farmer raising cattle has his own value chain for raising and processing the cattle. The shoemaker, then takes the leather from the farmer and produces a completely different product, enhancing the value proposition along the way.
In a similar fashion, as security professionals, we often take information from one system (for example: Syslog output) and enhance the value of that information by prioritizing

No comments yet.